Layer 8 Technology: How We Protect Users at our Plattsburgh Office
By A Mystery Man Writer
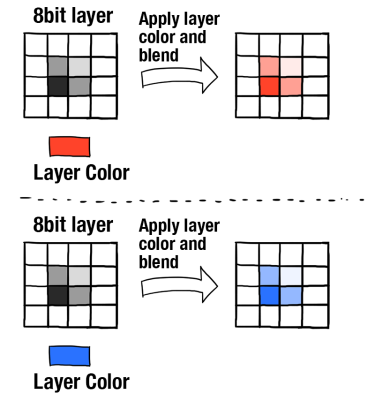
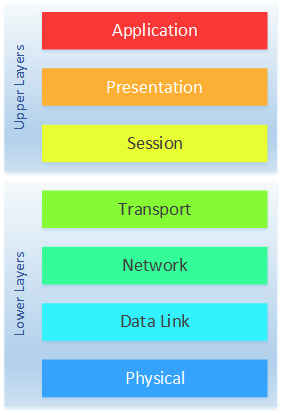
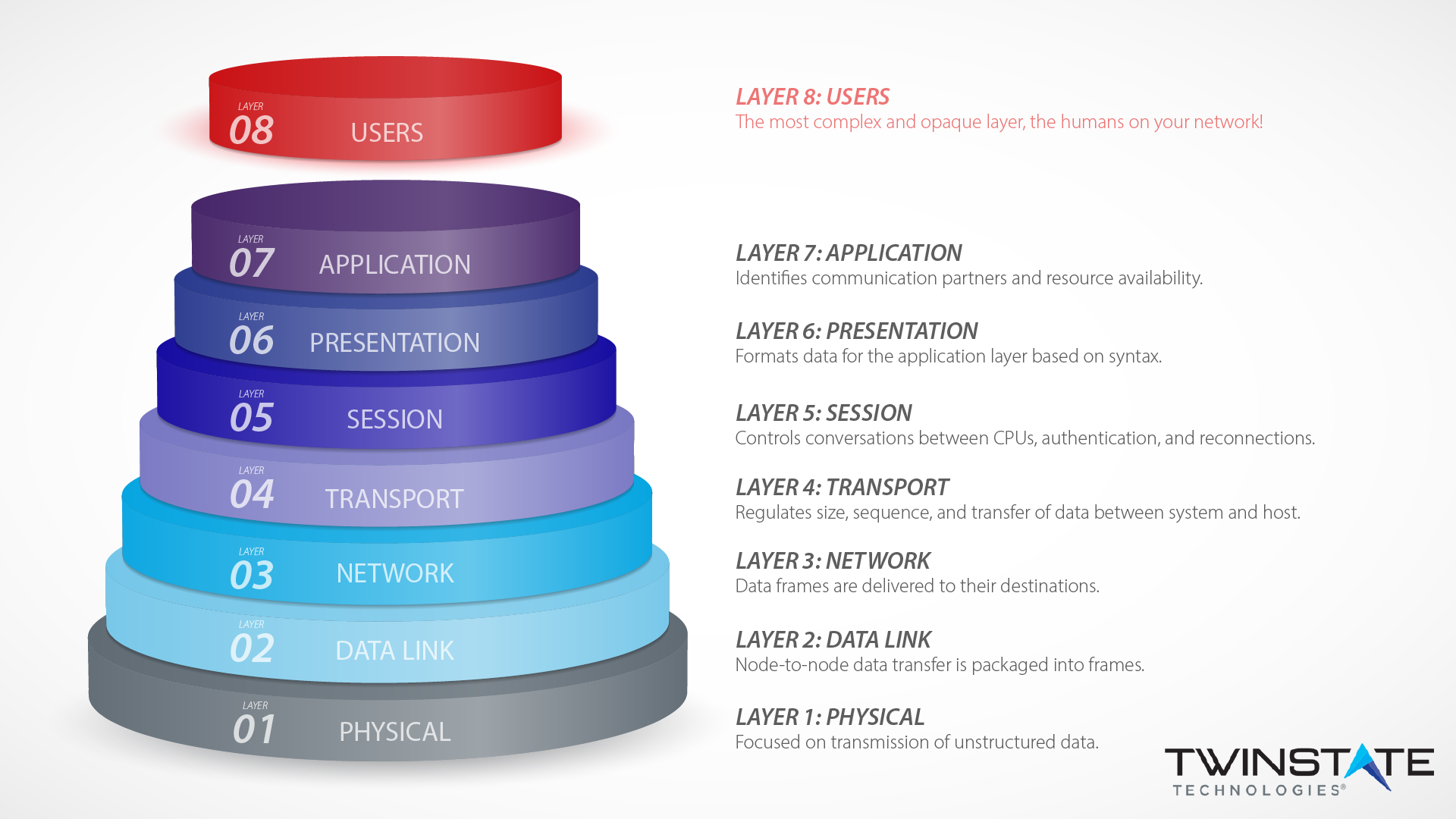
Layer eight security depends on end-users according to the OSI model. Learn how Twinstate Technologies protects the users at our Plattsburgh, NY office.
Conventional road hi-res stock photography and images - Alamy

BETA Technologies to launch major expansion in Plattsburgh

Usherwood Office Technology

The 8 layers of cyber security needed to protect your business

Cybersecurity Solutions

How Norsk Titanium Is Scaling Up AM Production — and Employment
The worst technology failures of 2023 - MIT Technology Review
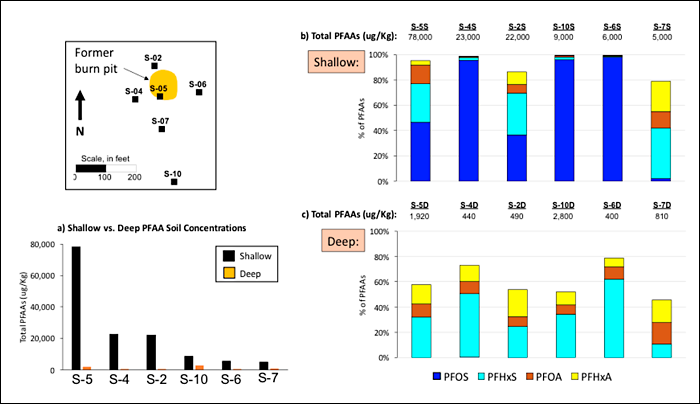
15 Case Studies – PFAS — Per- and Polyfluoroalkyl Substances

Packaging World May 2023 by PMMIMediaGroup - Issuu
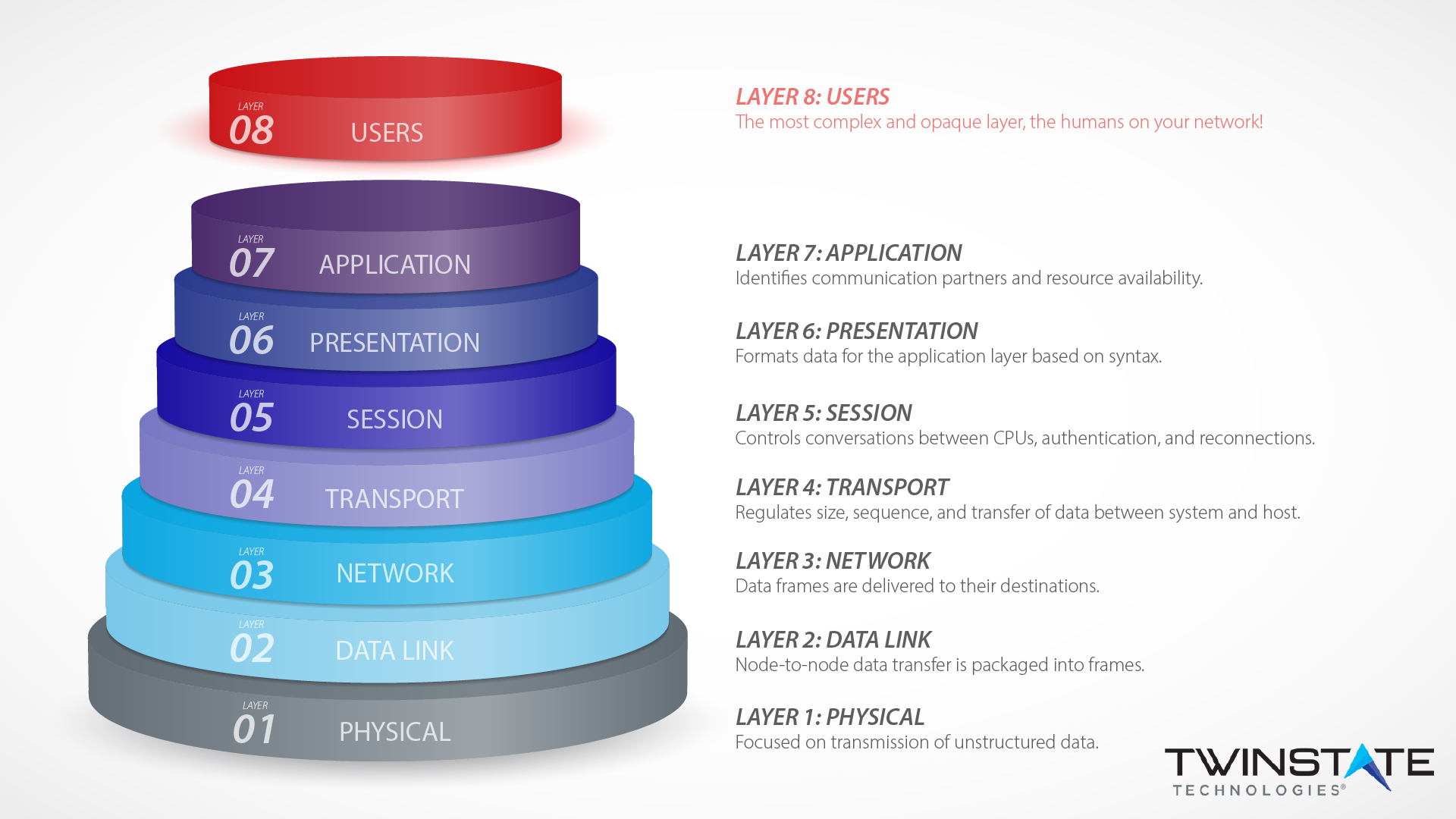
Layer 8 Technology: How We Protect Users at our Plattsburgh Office

8layer Technologies, Inc.

From Day One September Virtual: New Ideas for Successful
:format(jpg)/cloudfront-us-east-1.images.arcpublishing.com/coindesk/MN6DVCIS3JE25OULR6S2QPGWAI.jpg)
What Is Cryptojacking? How to Protect Yourself Against Crypto

Software Intellectual Property 101: IP Protection & More
All-Inclusive, Fully Outsourced IT Management
- Pokemon Pikachu Men's Panties Underwear Boxers Cartoon Anime Panties Breathable Men Underpants Comfortable Male Shorts Underwear - AliExpress

- Collette Pleated Babydoll Slip – Le Rose AU

- Black One Size Cup 38 Band Bras & Bra Sets for Women for sale

- Bigersell Tank Dress Pajamas for Women Casual Round Neck Sleeveless Bandage Stripe Printed Loose Tank Sling Dress Women Boho Dress Style 2615, Female Regular Dresses Green M

- Perfume gêmeo? Saiba se o Glamour Myriad, de O Boticário, tem cheiro parecido com Myriad, já fora de linha