Monday, Sept 30 2024
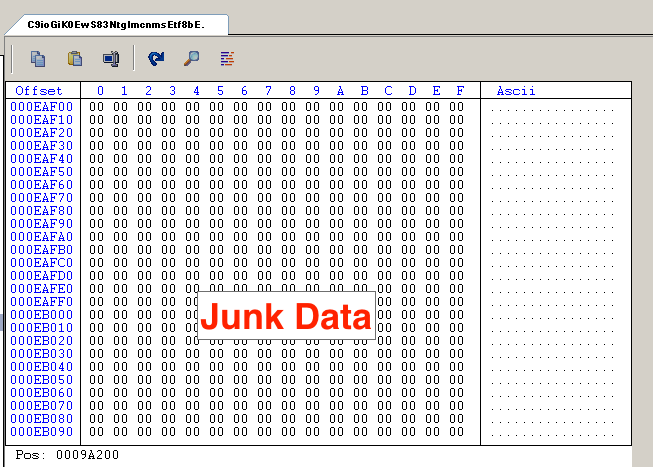
How Hackers Use Binary Padding to Outsmart Sandboxes
By A Mystery Man Writer

Hackers use pirated software to hijack Mac, Android, and Windows devices - CyberGuy

How Hackers Are Able To Outsmart Sandboxes

Detect Malware Associated with the Most Exploited CVEs - Intezer

7 Most Important AWS Security Tools - Intezer

Intezer - Blog

9 Tools to Use Right Now to Improve Azure Platform Security - Intezer

Roy Halevi (@royhalevi) / X

Emre KISA on LinkedIn: Indirect prompt injection, have you heard

How Hackers Use Binary Padding to Outsmart Sandboxes

Disarming visualization-based approaches in malware detection systems - ScienceDirect

Disarming visualization-based approaches in malware detection systems - ScienceDirect
Related searches
- conv neural network - Convolutional Layers: To pad or not to pad

- Dimora Silicone Foam Dressing Without Border 4x 4 Highly Absorbent Adhesive Wound Bandage Cuttable Pads for Wound Care 5 Pack

- CSS Padding: Advanced Guide to Master Spacing in Style

- Annoying Keyboard Overlaps: Understanding Flutter's Padding, vs
- GitHub - bytedance/effective_transformer: Running BERT without Padding
Related searches
©2016-2024, reintegratieinactie.nl, Inc. or its affiliates




